What is NIST SP 800-171 and why should government contractors care about it? This question often pops up in the minds of business owners, especially those dealing with sensitive information. As businesses continue to digitize their operations, cybersecurity has become a non-negotiable component of business strategy. This is where NIST SP 800-171 comes into play.
What is NIST 800-171?
NIST SP 800-171 is a NIST Special Publication that provides a set of standards for protecting the confidentiality of controlled unclassified information (CUI) in non-federal systems and organizations. NIST 800-171 was developed to ensure CUI is properly protected on a consistent basis across nonfederal systems among the Defense Industrial Base (DIB) to make sure that the federal government can carry out its missions.
Official Documentation: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
Understanding the core functions of the NIST Cybersecurity Framework
The NIST Cybersecurity Framework (CSF) contains five core functions. These functions provide a high-level, strategic view of your organization’s management of cybersecurity risk. They also help organize basic cybersecurity activities at their highest level which NIST 800-171 breaks down into a more comprehensive list of security controls we’ll go over in the next section.
The five functions are:
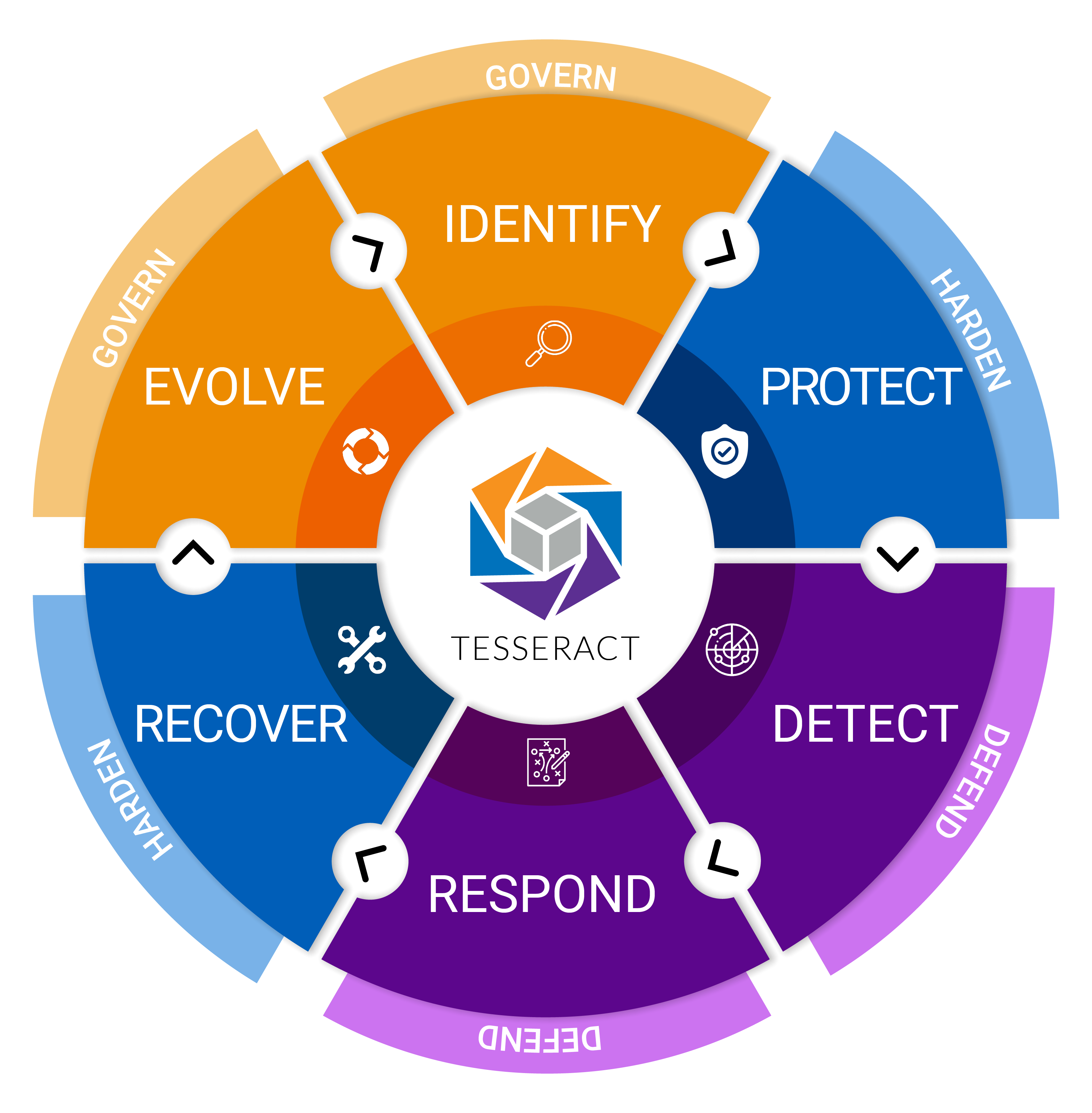
Identify: This function involves developing an organizational understanding of how to manage risks to systems, people, assets, data, and capabilities. It helps you understand your business context, the resources that support critical functions, and related cybersecurity risks to enable you to focus and prioritize your efforts.
Protect: This function outlines safeguards to ensure the delivery of critical services. It supports the ability to limit or contain the impact of a potential cybersecurity event.
Detect: This function involved implementing appropriate activities to identify the occurrence of a cybersecurity event quickly. The goal is to discover cybersecurity events in a timely manner to understand their potential impact and contain them.
Respond: This function focuses on developing and implementing appropriate activities to place regarding detecting a cybersecurity incident to ensure it is handled in a way that limits damage, increases the confidence of external stakeholders, and reduces recovery time and costs.
Recover: This function builds a plan for resilience by outlining how to restore any capabilities or services that are impaired due to a cybersecurity incident to restore normal operations as quickly as possible and minimize the impact to the business.
Key requirements of NIST 800-171
Access Control (AC)
Access Control is a fundamental requirement for dictating how CUI is accessed within an organization to minimize the risk of unauthorized or inadvertent exposure of sensitive data.
Awareness & Training (AT)
Awareness and Training refers to the need for educating your employees about the security risks associated with their roles and the necessary protocols to mitigate those risks.
Audit & Accountability (AU)
Audit and Accountability aims to ensure organizations can identify, respond to, and prevent unlawful or unauthorized activities involving CUI.
Configuration Management (CM)
Configuration Management emphasizes the need for maintaining standardized, secure configurations of your systems to protect CUI.
Identification & Authentication (IA)
Identification and Authentication focuses on ensuring that only verified users, processes, and devices can CUI within your organization.
Incident Response (IR)
Incident Response accentuates the need for a robust and effective response plan for security incidents involving CUI.
Maintenance (MA)
Maintenance stresses performing regular maintenance tasks on your systems to maintain the security and efficiency of operations involving CUI.
Media Protection (MP)
Media Protection highlights the importance of securing all types of media that contain CUI including how it’s accessed, stored, transported, and disposed of.
Personnel Security (PS)
Personnel Security emphasizes the need to manage risks associated with the people who have access to CUI.
Physical Protection (PE)
Physical Protection underscores the need for physical security measures to safeguard systems, facilities, and resources where CUI is processed, stored, or transmitted.
Risk Assessment (RA)
Risk Assessment focuses on the need for identifying, assessing, and managing risks to CUI and the systems that process, store, or transmit it.
Security Assessment (CA)
Security Assessment compels organizations to regularly evaluate the effectiveness of their security controls protecting CUI.
System & Communications Protection (SC)
System and Communications Protection stresses the importance of safeguarding information and the system and network levels, particularly where CUI is being transmitted.
System & Information (SI)
System and Information emphasizes the need to ensure and maintain the integrity of CUI and the systems that process, store, or transmit it.
Who needs to comply with NIST 800-171?
Any non-federal entity that handles, processes, stores, or transmits CUI should comply with NIST 800-171 standards. As of November 30, 2020, the DFARS clause 252.204-7012 requires defense contractors to implement the recommended requirements for NIST 800-171 compliance to ensure that they are providing the necessary security and protection of the covered defense information included in their defense contracts.
Steps to achieve NIST 800-171 compliance
NIST 800-171 self-assessment
Every defense contractor must meet the requirements of a Basic Assessment – a self-assessment using the organization’s existing System Security Plan (SSP) and Plan of Action and Milestones (POAM) to calculate their own score and then enter it on SPRS. The SPRS entry will consist of six fields: SSP name, CAGE code associated with the plan, a brief description of the plan architecture, date of the assessment, total score, and the date a score of 110 will be achieved. If you already have an SSP and POAM, it should take less than an hour to complete the Basic Assessment.
The results of your Basic Assessment will be key in helping you identify what CUI your organization handles, how it is currently protected, and where the gaps are in your protections that must be mitigated.
Develop an action plan
Once you’ve got a handle on the current state of your cybersecurity, or your cybersecurity posture, it’s time to formulate a comprehensive plan to bridge the gap between your current state and your desired state of compliance. Developing your action plan has several key steps:
- Prioritize identified deficiencies
- Define your goals and ensure that they are SMART (Specific, Measurable, Achievable, Relevant, and Timely)
- Identify the tasks and actions that must be taken
- Assign tasks to their responsible parties
- Set timelines for each task and be sure to allow for potential delays and/or challenges
- Monitor your progress by regularly reviewing your action plan and progress toward each goal
Implement security measures
With your plan in hand, or probably more realistically stored on your network, it’s now time to translate the steps in your action plan into tangible security controls and practices to safeguard your CUI. Implementing security measures can look like a number of key activities including:
- Establishing security controls
- Acquiring a CMMC RPO or MSP to perform technical tasks
- Updating policies and procedures
- Conducting training
- Monitoring implementation
Train staff
As evidenced by its own family of security controls in the NIST SP 800-171 standard, security awareness training crucial step to helping protect CUI within your organization. Proper security awareness training ensures your employees, especially those handling CUI, understand the security risks associated with their role and how to mitigate risks. Proper training will help mitigate human error and empower your employees to protect your business and your data.
Regular audits
Let’s begin by separating audits into two buckets. The first is the audits you conduct internally. These are regular audits conducted in intervals specified in your cybersecurity program manual. These audits help verify ongoing compliance, identify areas for improvement, and ensure your security measures remain effective in the changing threat landscape.
The second bucket of audits, or assessments, are conducted by the Defense Contract Management Agency (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), or other sanctioned bodies. You will recall we discussed a “Basic Assessment” earlier. This is an assessment you conduct yourself. Continuing from here, there are Medium and High Assessments that increase in scrutiny. It is estimated that roughly 200 organizations will go through a Medium Assessment each year from randomly selecting from the over 19000 companies with scores in SPRS and 110 unique organizations will go through a High Assessment each year.
Consequences of non-compliance with NIST 800-171
Non-compliance with NIST SP 800-171 can have severe consequences for defense contractors ranging from financial to reputational and legal ramifications. Some potential consequences include:
- Loss of government contracts
- Financial penalties
- Reputational damage
- Legal consequences
- Increased risk of data breaches
Getting help with NIST 800-171 compliance
Achieving NIST 800-171 compliance requires a deep understanding of your networks, security processes, and procedures, so much so that the National Institute of Standards and Technology (NIST) stated that “the first thing they should keep in mind is that being DFARS compliant likely involves working with a cybersecurity consultant that knows the NIST SP 800-171 requirements inside and out.”
The right cybersecurity compliance partner can help you implement the most comprehensive solution for your business by helping you write policies, implement technology, document your practices, assess business risk, and put into place the cyber program management needed to ensure you mature to meet the increasing demands on the Defense Industrial Base.
Ardalyst can help you jumpstart your NIST 800-171 compliance with our FREE Tesseract Program Trial. It begins with a Risk Assessment that meets the requirements for RA.L2-3.11.1 and lays the foundation for your program and next steps completely free. You will also receive:
- A preview of your System Security Plan (SSP) & Plan of Actions and Milestones (POAM)
- An overview of the Tesseract Managed Cybersecurity Program and your path to getting and staying compliant
- A technical design of your Tesseract program enclave
- Exclusive deals on additional tools like Microsoft GCC & GCC-High
You can also take advantage of our FREE NIST 800-171 Self-Assessment tool!
Frequently asked NIST 800-171 questions
What challenges might SMBs face in becoming NIST SP 800-171 compliant?
SMBs may face challenges such as a lack of resources, technical expertise, or awareness.
How often should audits be conducted for NIST SP 800-171 compliance?
Regular audits are recommended, with the frequency depending on the organization’s size, complexity, and the sensitivity of the CUI it handles. We recommend that audits be conducted at least annually.
How can NIST SP 800-171 compliance enhance customer trust?
Compliance demonstrates to customers that the organization takes data security seriously and is committed to protecting sensitive information.
Can NIST SP 800-171 compliance give my business a competitive edge?
Yes, demonstrating compliance with recognized security standards can differentiate your business from competitors and may be a requirement for certain contracts.
Why is staff training essential for NIST SP 800-171 compliance?
Staff training is crucial as employees play a key role in protecting CUI, and they must understand the security risks associated with their activities and the appropriate security protocols.



