There has been a lot of speculation about the Cybersecurity Maturity Model Certification (CMMC) in recent years. Some question whether it will ever be required. Others see its delay as a sign of failure. Whatever your thoughts, the lull we’re experiencing has fueled inactivity amongst the defense industrial base (DIB). Many small and midsize businesses are unsure what the right next steps are, what’s being required of them, and if it’s worth it. Below, we’ve answered some of our most frequently asked CMMC questions to help put an end to the indecision and ensure you’re making informed decisions.
What is the Cybersecurity Maturity Model Certification (CMMC) 2.0?
CMMC is described as a comprehensive framework to protect the DIB from increasingly frequent and complex cyberattacks. DoD’s goal is to safeguard sensitive unclassified national security information. This type of information is called Controlled Unclassified Information (CUI). CMMC 2.0, the most recent version of the framework was announced in November of 2021, providing an updated structure to that of CMMC 1.0.
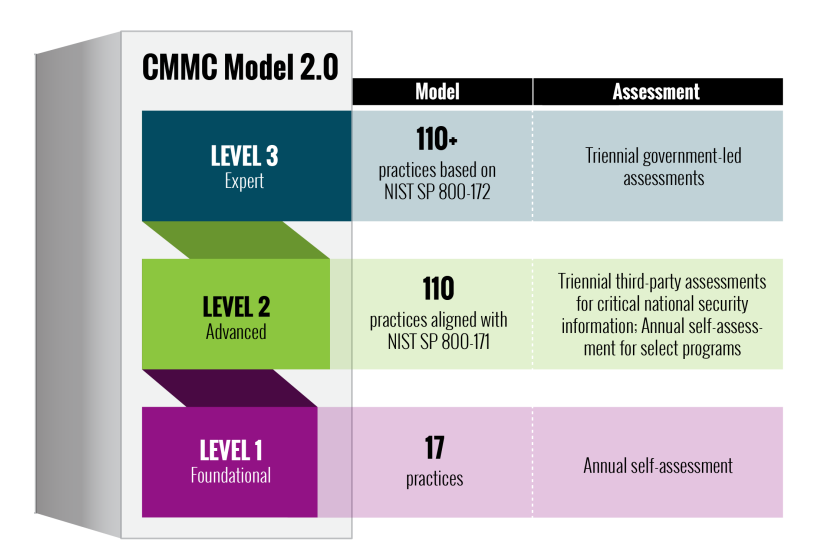
CMMC 2.0 consists of three levels.
Level 1 – Foundational: Contains 17 practices aligned with FAR 52.204-21 and is required for companies that only handle Federal Contract Information (FCI) and do not handle Controlled Unclassified Information (CUI).
Assessment: Level 1 only requires businesses to perform an annual self-assessment.
Level 2 – Advanced: Contains 110 practices aligned with NIST SP 800-171 required by defense contractors who handle and must safeguard CUI.
Assessment: Level 2 requires a triennial third-party assessment by a Certified Third-Party Assessment Organization or C3PAO.
Level 3 – Expert: Contains the same 110 practices of CMMC 2.0 Level 2 and adds controls from NIST SP 800-172 demonstrating a greater depth of protection of critical national security information and reducing the risks of exploitation by Advanced Persistent Threats (APTs).
Assessment: Level 3 requires a triennial assessment by the U.S. government. Assessments will be conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
Do I actually need to worry about CMMC?
The short answer is yes! It’s important to remember that CMMC is certifying that security standards have been met, like those of NIST SP 800-171 for CMMC 2.0 level 2. Under CMMC 2.0, there are no new security controls. CMMC is an assessment regime for existing requirements.
Regardless of CMMC’s status, defense contractors who handle controlled unclassified information (CUI) as part of their work with federal and state agencies will still find DFARS 252.204.7019 clauses in their contracts.
The DFARS 252.204-7019 clause, which has been in effect since November 30, 2020, states that the contractor must comply with NIST 800-171 requirements, complete a self-assessment of their ability to meet those requirements resulting in a score that must then be submitted to the Suppliers Performance Risk System (SPRS), along with a System Security Plan (SSP) and a Plan of Action and Milestones (POAM). This means that whether your business seeks out an official assessment to be certified at CMMC level 2 or not, the requirements for your cybersecurity program remain the same.
Why is CMMC a priority?
There are two sides to the CMMC coin. On one side, the United States is under persistent attack. For cyber attackers who would wish to do our nation harm, the easiest way is often through the supply chain where security standards aren’t consistent, and defenses are usually much easier to penetrate than that of the government’s own IT infrastructure.
This makes targets of nearly everyone from technology firms like Microsoft and SolarWinds, to critical infrastructures like that of the colonial pipeline, and especially small and mid-sized contractors who often lack the knowledge and resources to properly protect themselves. Implementing security standards like NIST 800-171 and certifications of those standards like CMMC help ensure that our nation and all who support it are doing their part to protect it.
The other side to the CMMC coin is you! When you make CMMC a priority, you make your business, your data, and your customers a priority. Threat actors are getting smarter all the time, and customers are demanding better, more integrated, more convenient, and more optimized digital experiences. In our increasingly digital business landscape, being able to demonstrate good cyber hygiene and security to your clients and customers is key. As good cybersecurity practices become a requirement of customers, the investment becomes a revenue driver, not just a cost. Being proactive about your cyber hygiene now can improve both your reputation and financial stability.
What happens if I’m not compliant?
There are multiple angles to which this question must be answered. From a contracting standpoint, you won’t be a viable candidate without compliance. Even in a CMMC-less world, failing to meet NIST 800-171 cybersecurity standards currently has a negative impact on your business. Scores submitted into SPRS are visible to federal and state agencies and can be a factor when deciding to award contracts. Once CMMC is finalized, certification at any of the 3 CMMC levels will instantly demonstrate a certain level of “good” cyber hygiene and assure federal and state agencies that you’re doing your part to keep their data safe. However, getting started soon is going to be critical. Once CMMC rulemaking is done, if you haven’t already started seeking an assessment, you may find that getting one scheduled is difficult in the last-minute rush.
Failing to comply with CMMC, or any cybersecurity standard, increases your risk of a damaging attack. The requirements outlined in these standards are the foundation for good cyber hygiene and the starting point for how you’d measure your business’s security — with or without a compliance mandate. Taking these measures for your business ensures your data, devices, and networks are protected from attacks like ransomware, malware, and more, the proper contingency plans are in place for business continuity, and your employees are properly trained to ensure they know how to maintain the integrity of your cybersecurity efforts.
On the extreme end, the government has indicated that it will use the False Claims Act to prosecute organizations that submit false attestations.
With all these new requirements, should I just shift to providing commercial services only?
Some DIB companies are considering switching to commercial work to avoid these requirements. In many industries, this might delay the cybersecurity investment for a year, but it won’t eliminate it. National legislation on incident reporting, discussion of expanding CMMC-like requirements across all Critical Infrastructure industries, and commercial supply chain risk reduction programs mean that improving your cybersecurity programs will be a requirement for most businesses in the future.
How do I get compliant?
There is no one-size-fits-all solution when it comes to compliance. How you address the requirements of CMMC should be specific to your unique business to ensure that your cybersecurity is a business enabler and not an inhibitor. To do so, start with a cybersecurity assessment to figure out where your unique gaps are. Our team of CMMC-AB Registered Partitioners can walk you through a free compliance consultation to provide a preliminary score out of the 110 controls (this is the score you need to upload to SPRS) and a summary report of their findings that you can incorporate into your SSP and POAM. From here, we can make recommendations for next steps and help you get started with a comprehensive managed cybersecurity program. Contact us online at www.tesseract.ardalyst.com, email us at info@ardalyst.com, or call us at (833) 682-8270 to schedule your free consultation today.