The Department of Defense (DoD) has recently published a proposed rule of the Cybersecurity Maturity Model Certification (CMMC) program, marking a pivotal development in the realm of defense contracting and cybersecurity. This initiative marks a significant step in the evolution of cybersecurity standards that define how defense contractors must safeguard sensitive information. The CMMC 2.0 proposed rule, specifically, is set to transform the landscape of cybersecurity compliance within the defense industry. This article aims to unpack the nuances of the CMMC 2.0 proposed rule and its implications for those operating in the defense sector.
Background of CMMC
The CMMC framework was originally introduced to enhance cybersecurity measures within the Defense Industrial Base (DIB). It stemmed from growing concerns about the protection of Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) against cyber threats along the DoD’s supply chain.
CMMC 1.0, while comprehensive, faced criticism for its complexity and the burden it placed on contractors, especially smaller businesses. Companies argued that this complexity would result in significant costs and a lengthy compliance process, potentially stifling both innovation and participation among small players in the DIB.
Major Developments in CMMC 2.0
CMMC 2.0 made its initial debut on November 4, 2023, with some important initial changes over 1.0 that are still true today:
- Simplified Compliance Process: The updates have realigned the requirements to the existing DFARS 252.204-7012 reliance on NIST 800-171 without any additional security or maturity controls. Since organizations have known about the 800-171 requirements since 2017, this change addressed concerns about additional costs.
- Clarification on the use of POAMs: The proposed regime under CMMC 1.0 would not allow for the use of POAMs, or Plans of Action and Milestones that indicate what a contractor would need to do to reach full compliance should they not have every security control in place. CMMC 2.0’s rules specify which controls may be on the POAM and provide a deadline for implementation (see below for details).
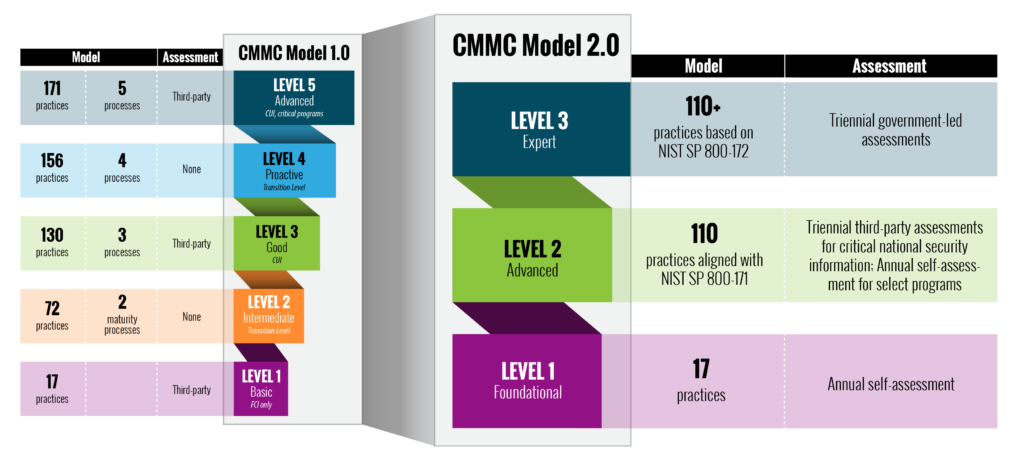
- Reduction in Compliance Levels: The number of security compliance levels has been reduced from five to three. This revision has removed the previous second and fourth levels, resulting in a new structured model: Level 1 (Foundational), Level 2 (Advanced), and Level 3 (Expert).
- Level 1 (Foundational): Level 1 mirrors the initial version’s structure. Organizations handling only Federal Contract Information (FCI) are required to implement 17 specific practices in alignment with FAR 52.204-21. These practices are aimed at establishing basic cyber hygiene. These companies are expected to conduct an annual self-assessment to ensure they meet the foundational level requirements.
- Level 2 (Advanced): Level 2 corresponds to the third level in the previous version, and aligns to the existing requirements in DFARS 252.204-7012. This level includes a set of 110 practices in line with the standards set out in NIST SP 800-171, Rev 2 (this is important to note as NIST has recently issued Revision 3). These practices are essential for defense contractors managing Controlled Unclassified Information (CUI). To attain certification at this level, organizations undergo assessments every three years, conducted by Certified Third-Party Assessment Organizations (C3PAOs).
- Level 3 (Expert): Level 3, equivalent to the fifth level in the original framework, encompasses all practices from Level 2 plus additional measures based on NIST SP 800-172 (still in draft status). These extra requirements are designed to provide enhanced protection for critical national security information, specifically addressing risks posed by Advanced Persistent Threats (APTs). Organizations at this level must have their cybersecurity programs assessed triennially led by the Defense Contract Management Agency Cybersecurity Assessment Center (DIBCAC).
- Self-Assessments: Level 1 contractors, who previously needed third-party assessments, can now conduct annual self-assessments. This is especially relevant for many DoD contractors who do not handle Controlled Unclassified Information, and who may not have the resources for extensive external assessments. The government has also stated that certain Level 2 programs may allow for self-assessment.
Read more about key CMMC 2.0 changes here.
Key Features of the Proposed Rule
The Role of a POAM
A Plan of Action and Milestones (POAM) is a document used within the context of information security management and compliance, particularly in the government and defense sectors. It serves as a critical tool for organizations to outline and track the actions they need to take to address and mitigate identified security vulnerabilities. For Level 2, contractors can utilize POAMs. However, POAMS are not permitted for security requirements with a point value greater than 1 except for SC.L2-3.13.11 CUI Encryption if it has a value of 1 or 3; and none of the following security requirements are also included in the POAM:
- AC.L2-3.1.20 External Connections (CUI Data)
- AC.L2-3.1.22 Control Public Information (CUI Data)
- PE.L2-3.10.3 Escort Visitors (CUI Data)
- PE.L2-3.10.4 Physical Access Logs (CUI Data)
- PE.L2-3.10.5 Manage Physical Access (CUI Data)
Unimplemented security controls are also subject to a time constraint and must be resolved within 180 days following the initial evaluation. POAMs are not applicable for Level 1.
Access the full list of security controls that must be excluded from your POAM here.
Requirement Flow Down
The responsibility of prime contractors now extends to ensuring that the CMMC requirements are passed down to their subcontractors and further down to any lower-tier subcontractors who will be handling (processing, storing, or transmitting) Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).
The rule sets the baseline CMMC level for subcontractors based on the prime contractor’s CMMC level and the type of information handled. For subcontractors dealing exclusively with FCI, a Level 1 certification is necessary. In contrast, subcontractors handling CUI must meet at least a Level 2 Self-Assessment, depending on the prime contractor’s certification level. If the prime contractor is required to have a Level 2 or Level 3 Certification Assessment and the subcontractor processes, stores, or transmits CUI, the subcontractor is obligated to have a minimum of a Level 2 Certification Assessment.
Timeline for Implementation
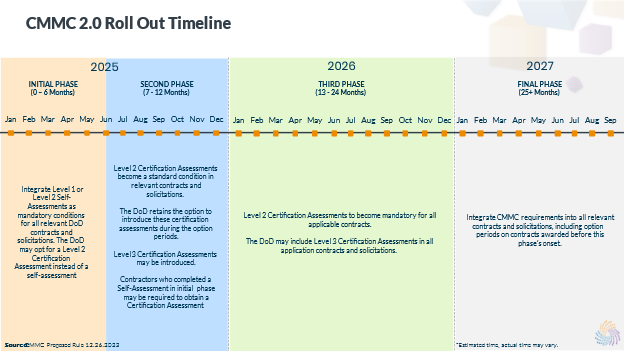
The DoD is planning a systematic and staged introduction of CMMC requirements across new contracts and existing ones during their option periods. This phased implementation is expected to span three years and include four distinct phases, starting in January 2025:
- 2025 JAN – Initial Phase (First 6 Months): Commencing with the update to DFARS 252.204-7021, the DoD plans to integrate Level 1 or Level 2 Self-Assessments as mandatory conditions for all relevant DoD contracts and solicitations. In some cases, the DoD might opt for a Level 2 Certification Assessment instead of a self-assessment. These requirements could extend to the option periods of contracts awarded before the DFARS revision.
- 2025 JUL – Second Phase (Months 7-12): The DoD intends to escalate the requirements by making Level 2 Certification Assessments a standard condition in relevant contracts and solicitations. During this phase, the DoD retains the option to introduce these certification assessments during the option periods instead. There’s also the possibility of introducing Level 3 Certification Assessments during this phase. Contractors who completed a Self-Assessment in the first phase may find themselves facing a Certification Assessment soon after.
- 2026 JAN – Third Phase (Months 13-24): Level 2 Certification Assessments are expected to become mandatory for all applicable contracts, both as a condition of award and for exercising option periods on contracts predating the DFARS revision. The DoD may also include Level 3 Certification Assessments in all applicable contracts and solicitations, with the option to delay their introduction to option periods.
- 2027 JAN – Final Phase (Months 25 and Beyond): The DoD plans to integrate CMMC requirements comprehensively into all relevant contracts and solicitations. This includes option periods on contracts awarded before this phase’s onset. The full implementation, covering all phases, is anticipated to be completed by 2027.
Cost Implications for Your Business
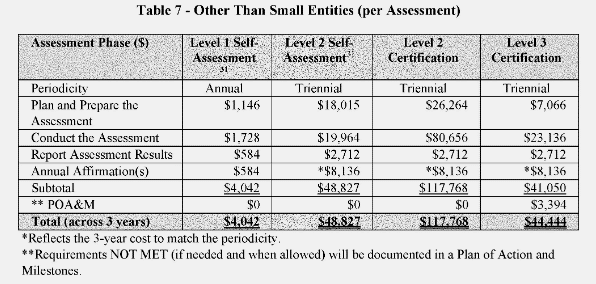
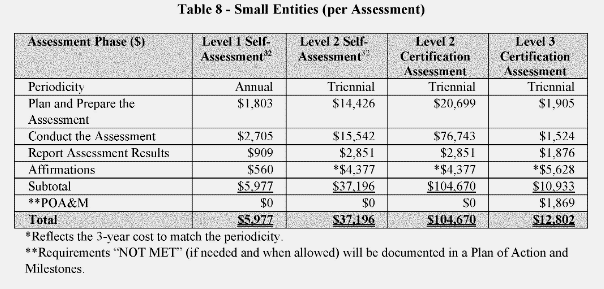
The proposed rule outlines specific costs for conducting CMMC assessments and certification processes. For instance, a three-year Level 2 assessment is estimated to cost larger firms approximately $118,000 and smaller firms around $105,000. The rule does not account for the costs of adhering to existing cybersecurity standards for FCI and CUI as outlined in FAR 52.204-21 and DFARS 252.204-7012, assuming these are pre-existing expenses. Contractors should be aware that the costs incurred for CMMC assessments are separate from the costs of implementing standards like NIST SP 800-171. The rule also mandates contractors and subcontractors to undergo certification assessments by C3PAOs for certain CMMC levels, which incurs significant costs for both small and large businesses. The rule acknowledges these costs may be recoverable in some contract types but does not specify a reimbursement process for pre-award expenses. Though the financial burden can be significant, it’s important to remember that compliance can be a competitive advantage in federal contracting.
Assessments & Appeals
After diligently preparing to meet the necessary CMMC level, arranging, and financing your C3PAO evaluation, it can be disheartening to receive unsatisfactory results that you believe are incorrect. Thankfully, the proposed CMMC rule outlines an appeals process for assessments, aligning with ISO/IEC standards 17020:2012 and 17011:2017. Contractors can appeal a C3PAO Certification Assessment through a set process. The C3PAO will initially handle disputes internally, with a review by personnel not involved in the original assessment. If unresolved, the dispute advances to the Accreditation Body for a final decision. Similarly, DIBCAC Certification Assessments can be appealed and reviewed by DIBCAC. This system provides a structured method for contractors to contest assessment results, ensuring fairness and accountability in the certification process.
Another important addition to note regarding Assessments is that the new proposed rule indicates that the Department of Defense (DoD) has the discretion to exempt certain procurements from the mandatory CMMC third-party assessments. However, it also clarifies that there isn’t a formal process for companies to request exemptions from the CMMC requirements themselves.
Guidelines for Cloud Service Providers & External Service Providers
The proposed CMMC rule includes specific guidelines for Cloud Service Providers (CSPs) and External Service Providers (ESPs) used by contractors. CSPs must ensure their services, if used to handle Controlled Unclassified Information (CUI), comply with FedRAMP Moderate standards or equivalent. ESPs, including outsourced IT and cybersecurity services, must also meet the required CMMC level for the contract they support. This includes having security measures documented in the contractor’s System Security Plan (SSP). These requirements ensure that both CSPs and ESPs maintain a cybersecurity standard compatible with the CMMC level required for the defense contract they are part of.
Conclusion & Recommendations
As of this post’s composition, the proposed CMMC rule is open for public feedback until February 26, 2024. The DoD plans to gradually roll out CMMC, starting with some pilot contracts in 2025 and aiming for full implementation by 2026. Given this timeline, businesses should start preparing as it could take considerable time, typically 12 to 36 months, to meet these stringent requirements.
What Ardalyst is Doing
Ardalyst is a cybersecurity firm providing services to the federal government. Our founders are veterans and entrepreneurs who are committed to ensuring that businesses of all sizes have access to cybersecurity solutions that are cost-effective and easy to implement. For four years, since the introduction of draft versions of CMMC 1.0, we have been helping small and mid-sized businesses meet existing NIST 800-171 compliance requirements and prepare for CMMC.
Our experience has led to the development of a cybersecurity-program-as-a-service model named Tesseract, designed to assist small and mid-sized businesses in complying with CMMC affordably. We also provide free resources for initiating NIST 800-171/CMMC compliance, including risk assessments and program design.
If you haven’t gotten started with your NIST 800-171/CMMC compliance, take advantage of our free resources to get you started.
- Get your free risk assessment. Meet the requirements for RA.L2-3.11.1 and lay out the foundation for your comprehensive cybersecurity program.
- Start your free Tesseract program design. Not only receive your free assessment of your current cybersecurity posture, but you’ll also get a:
- An overview of the Tesseract Managed Cybersecurity Program and your path to getting & staying compliant
- A technical design of your Tesseract program enclave
- A migration plan for implementation of your Tesseract enclave
- Exclusive deals on additional tools like Microsoft 365.